SPRUJC1 April 2024
- 1
- Abstract
- Trademarks
- 1Introduction
-
2Steps to Unlock JTAG for HSM Core With
TRACE32
- 2.1 Modifying the SCI Client Default Security Board Configuration
- 2.2 Building the SCI Client Security Board Configuration
- 2.3 Modifying the Secondary Bootloader’s x509 Certificate
- 2.4 Building the Secondary Bootloader
- 2.5 Verifying Secondary Bootloader and TIFS is Executing
- 2.6 Creating a Downloadable x509 Certificate With a Debug Extension
- 2.7 Execution of TRACE32 Unlock Script
- 2.8 Attaching to HSM Core With TRACE32
2.5 Verifying Secondary Bootloader and TIFS is Executing
Since the ROM Loader is not capable of unlocking JTAG for the HSM it is necessary to confirm the SBL is successfully booting and the TI Foundational Secure (TIFS) firmware is running. In order to validate this, copy or flash the newly built SBL image and TIFS binary to your non-volatile boot media. Next, connect to the MCU UART port on your board, power on the device, and verify with a terminal window that TIFS is running successfully (see Figure 2-6).
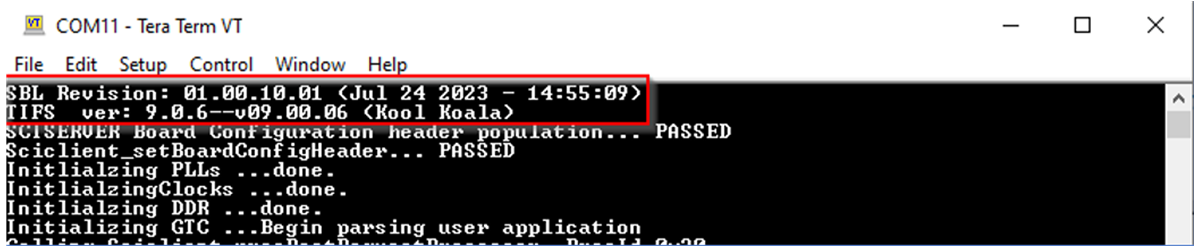 Figure 2-6 Verifying SBL and TIFS
Boot
Figure 2-6 Verifying SBL and TIFS
Boot