SSZTAA6 march 2017 CC3120
- 1
-
2
- 3
- Are there IoT applications that don’t need to implement security measures?
- Should IoT security features primarily focus on Wi-Fi and internet-level encryption of packets sent over the air?
- Do you need to use a high-end microprocessor unit (MPU) or dedicated secure element to effectively protect your products against potential risks?
If you’re an Internet of Things (IoT) designer, you’re probably often challenged to do more with less when it comes to security, constantly looking for new ways to protect your products against an ever-growing list of threats with lean system resources and perhaps limited experience.
Knowing that these struggles are very real, in this post I’ll outline a few top IoT security risks and common misconceptions on how to address them. I will also provide an overview of how new SimpleLink™ Wi-Fi® products give you more tools to help address security challenges through a novel architecture and rich set of integrated security features.
Are there IoT applications that don’t need to implement security measures?
Recognizing these threats, TI’s SimpleLink™ Wi-Fi® CC3220 wireless microcontroller (MCU) integrates a host of powerful, multilayered and hardware-based security features to provide you with powerful tools to help protect products from attacks such as local or remote packet sniffing, man-in-the-middle (MITM) server emulation, hostile takeovers via over-the-air updates, remote file manipulation, data and software theft, intellectual property (IP) cloning, and many more.
Should IoT security features primarily focus on Wi-Fi and internet-level encryption of packets sent over the air?

The CC3220 device actually integrates more than 25 additional security features to help provide tools that address potential threats from the larger end-to-end IoT landscape. Figure 2 portrays many of these features.
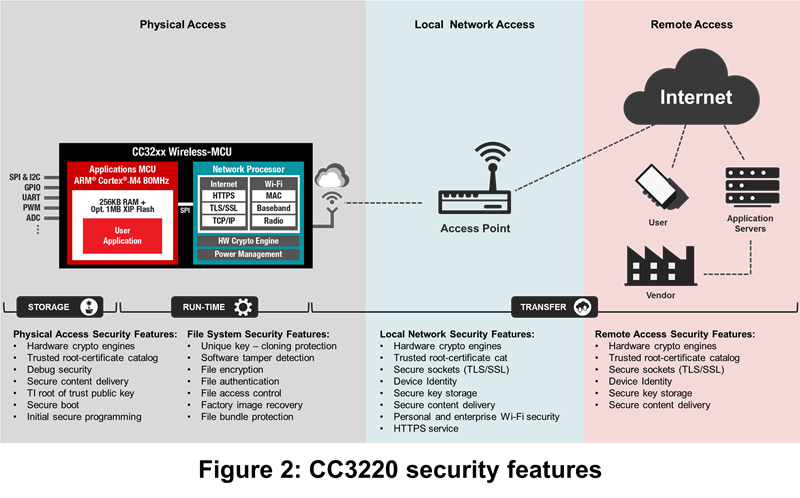
Do you need to use a high-end microprocessor unit (MPU) or dedicated secure element to effectively protect your products against potential risks?
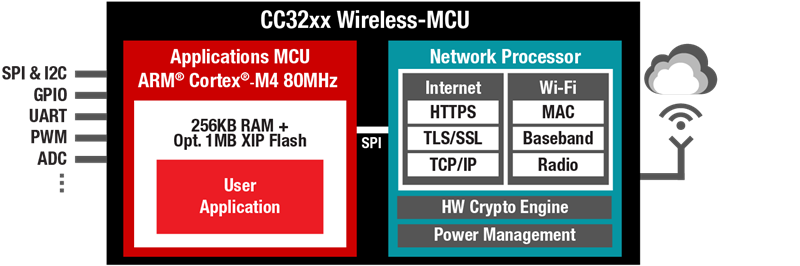
- Offload the processing of the device’s security functionality (including secure file system management) to the network processor and hardware cryptographic engines. This enables the million instructions per second (MIPS) and application MCU memory to be solely dedicated to the host application.
- Help reduce the firmware and network-management vulnerability for application-related risks by physically partitioning the programmable application MCU from the read-only memory (ROM)-based network processor
For more information about the CC3220 device, be sure to check out the product page and the broader SimpleLink Wi-Fi security documentation, including the full security application note, “SimpleLink CC3120, CC3220 Wi-Fi Internet-on-a-Chip Solution Built-In Security Features.”