SFFS779 December 2024 TMS320F28P550SJ
- 1
- 1Introduction
- Trademarks
- 2 TMS320F28P55x Product Safety Capability and Constraints
- 3TI Development Process for Management of Systematic Faults
-
4
TMS320F28P55x Component Overview
- 4.1 Targeted Applications
- 4.2 Hardware Component Functional Safety Concept
- 4.3 TMS320F28P55x MCU Safety Implementation
- 4.4 TMS320F28P55x Diagnostic Libraries
- 4.5 Functional Safety Constraints and Assumptions
-
5Description of Safety Elements
- 5.1 C2000 MCU Infrastructure Components
- 5.2 Processing Elements
- 5.3 Memory (Flash, SRAM and ROM)
- 5.4 On-Chip Communication Including Bus-Arbitration
- 5.5 Digital I/O
- 5.6 Analog I/O
- 5.7 Data Transmission
- 5.8 Not Safety Related Elements
-
6Management of Random Faults
- 6.1 Fault Reporting
- 6.2 Suggestions for Improving Freedom From Interference
- 6.3 Suggestions for Addressing Common Cause Failures
- 6.4
Descriptions of Functional Safety
Mechanisms
- 6.4.1
C2000 MCU Infrastructure Components
- 6.4.1.1 External Voltage Supervisor
- 6.4.1.2 External Watchdog
- 6.4.1.3 Multibit Enable Keys for Control Registers
- 6.4.1.4 Lock Mechanism for Control Registers
- 6.4.1.5 Software Readback of Written Configuration
- 6.4.1.6 Periodic Software Readback of Static Configuration Registers
- 6.4.1.7 Online Monitoring of Temperature
- 6.4.1.8 EALLOW and MEALLOW Protection for Critical Registers
- 6.4.1.9 Internal Watchdog (WD)
- 6.4.1.10 Brownout Reset (BOR)
- 6.4.1.11 Missing Clock Detect (MCD)
- 6.4.1.12 Clock Integrity Check Using CPU Timer
- 6.4.1.13 Clock Integrity Check Using HRPWM
- 6.4.1.14 External Clock Monitoring Using XCLKOUT
- 6.4.1.15 Software Test of Watchdog (WD) Operation
- 6.4.1.16 Software Test of Missing Clock Detect Functionality
- 6.4.1.17 PLL Lock Profiling Using On-Chip Timer
- 6.4.1.18 Peripheral Clock Gating (PCLKCR)
- 6.4.1.19 Dual Clock Comparator (DCC) – Type 2
- 6.4.1.20 Clock Integrity Check Using DCC
- 6.4.1.21 PLL Lock Indication
- 6.4.1.22 Software Test of DCC Functionality Including Error Tests
- 6.4.1.23 External Clock Monitoring Using XCLKOUT
- 6.4.1.24 Software Test of PLL Functionality Including Error Tests
- 6.4.1.25 Interleaving of FSM States
- 6.4.1.26 External Monitoring of Warm Reset (XRSn)
- 6.4.1.27 Reset Cause Information
- 6.4.1.28 Glitch Filtering on Reset Pins
- 6.4.1.29 NMIWD Shadow Registers
- 6.4.1.30 NMIWD Reset Functionality
- 6.4.1.31 Peripheral Soft Reset (SOFTPRES)
- 6.4.1.32 Software Test of ERRORSTS Functionality
- 6.4.1.33 Software Test of Reset – Type 1
- 6.4.1.34 Peripheral Access Protection – Type 1
- 6.4.1.35 Hardware Disable of JTAG Port
- 6.4.1.36 Lockout of JTAG Access Using OTP
- 6.4.1.37 Decryption of Encrypted Data Output Using Same KEY and IV
- 6.4.1.38 Information Redundancy Techniques Including End-to-End Safing
- 6.4.1.39 Transmission Redundancy
- 6.4.1.40 Disabling of Unused DMA Trigger Sources
- 6.4.1.41 Software Test of Function Including Error Tests
- 6.4.1.42 Software Test of Standalone GHASH Operation
- 6.4.2
Processing Elements
- 6.4.2.1 Reciprocal Comparison by Software
- 6.4.2.2 Software Test of CPU
- 6.4.2.3 Periodic Software Readback of Static Configuration Registers
- 6.4.2.4 Access Protection Mechanism for Memories
- 6.4.2.5 Hardware Disable of JTAG Port
- 6.4.2.6 CPU Handling of Illegal Operation, Illegal Results, and Instruction Trapping
- 6.4.2.7 Internal Watchdog (WD)
- 6.4.2.8 External Watchdog
- 6.4.2.9 Information Redundancy Techniques
- 6.4.2.10 Stack Overflow Detection
- 6.4.2.11 VCRC Auto Coverage
- 6.4.2.12 Embedded Real Time Analysis and Diagnostic (ERAD)
- 6.4.2.13 Inbuilt Hardware Redundancy in ERAD Bus Comparator Module
- 6.4.2.14 Software Test of CLA
- 6.4.2.15 CLA Handling of Illegal Operation and Illegal Results
- 6.4.2.16 Software Readback of Written Configuration
- 6.4.2.17 CLA Liveness Check Using CPU
- 6.4.2.18 Software Test of Function Including Error Tests
- 6.4.3
Memory (Flash, SRAM and ROM)
- 6.4.3.1 SRAM ECC
- 6.4.3.2 SRAM Parity
- 6.4.3.3 Software Test of SRAM
- 6.4.3.4 Bit Multiplexing in SRAM Memory Array
- 6.4.3.5 Periodic Software Readback of Static Configuration Registers
- 6.4.3.6 Software Readback of Written Configuration
- 6.4.3.7 Data Scrubbing to Detect/Correct Memory Errors
- 6.4.3.8 VCRC Check of Static Memory Contents
- 6.4.3.9 Software Test of Function Including Error Tests
- 6.4.3.10 Access Protection Mechanism for Memories
- 6.4.3.11 Lock Mechanism for Control Registers
- 6.4.3.12 Software Test of ECC Logic
- 6.4.3.13 Software Test of Parity Logic
- 6.4.3.14 Information Redundancy Techniques
- 6.4.3.15 CPU Handling of Illegal Operation, Illegal Results, and Instruction Trapping
- 6.4.3.16 Internal Watchdog (WD)
- 6.4.3.17 External Watchdog
- 6.4.3.18 CLA Handling of Illegal Operation and Illegal Results
- 6.4.3.19 Memory Power-On Self-Test (MPOST)
- 6.4.3.20 Power-Up Pre-Operational Security Checks
- 6.4.3.21 ROM Parity
- 6.4.3.22 Flash ECC
- 6.4.3.23 Flash Program Verify and Erase Verify Check
- 6.4.3.24 Flash Program and Erase Protection
- 6.4.3.25 Flash Wrapper Error and Status Reporting
- 6.4.3.26 Prevent 0 to 1 Transition Using Program Command
- 6.4.3.27 On-demand Software Program Verify and Blank Check
- 6.4.3.28 Software Readback of Written Configuration
- 6.4.3.29 CMDWEPROT* and Program Command Data Buffer Registers Self-Clear After Command Execution
- 6.4.3.30 ECC Generation and Checker Logic is Separate in Hardware
- 6.4.3.31 Bit Multiplexing in Flash Memory Array
- 6.4.3.32 Auto ECC Generation Override
- 6.4.3.33 Software Test of Flash Prefetch, Data Cache, and Wait States
- 6.4.3.34 Software Test of ECC Logic
- 6.4.4
On-Chip Communication Including Bus-Arbitration
- 6.4.4.1 Software Test of Function Including Error Tests
- 6.4.4.2 Internal Watchdog (WD)
- 6.4.4.3 External Watchdog
- 6.4.4.4 Periodic Software Readback of Static Configuration Registers
- 6.4.4.5 Software Readback of Written Configuration
- 6.4.4.6 CPU Handling of Illegal Operation, Illegal Results, and Instruction Trapping
- 6.4.4.7 CLA Handling of Illegal Operation and Illegal Results
- 6.4.4.8 Transmission Redundancy
- 6.4.4.9 Hardware Redundancy
- 6.4.4.10 EALLOW and MEALLOW Protection for Critical Registers
- 6.4.4.11 Information Redundancy Techniques
- 6.4.4.12 DMA Overflow Interrupt
- 6.4.4.13 Access Protection Mechanism for Memories
- 6.4.4.14 Disabling of Unused DMA Trigger Sources
- 6.4.4.15 Software Test of SRAM
- 6.4.4.16 Software Test of ePIE Operation Including Error Tests
- 6.4.4.17 Maintaining Interrupt Handler for Unused Interrupts
- 6.4.4.18 Online Monitoring of Interrupts and Events
- 6.4.4.19 SRAM Parity
- 6.4.4.20 Software Test of Parity Logic
- 6.4.4.21 Multibit Enable Keys for Control Registers
- 6.4.4.22 Majority Voting and Error Detection of Link Pointer
- 6.4.4.23 VCRC Check of Static Memory Contents
- 6.4.4.24 Software Check of X-BAR Flag
- 6.4.4.25 1oo2 Software Voting Using Secondary Free Running Counter
- 6.4.4.26 Software Test of Function Including Error Tests
- 6.4.4.27 Monitoring of CLB by eCAP or eQEP
- 6.4.4.28 Lock Mechanism for Control Registers
- 6.4.4.29 Periodic Software Read Back of SPI Buffer
- 6.4.5
Digital I/O
- 6.4.5.1 Software Test of Function Including Error Tests
- 6.4.5.2 Hardware Redundancy
- 6.4.5.3 Monitoring of ePWM by eCAP
- 6.4.5.4 Periodic Software Readback of Static Configuration Registers
- 6.4.5.5 Software Readback of Written Configuration
- 6.4.5.6 Lock Mechanism for Control Registers
- 6.4.5.7 ePWM Fault Detection Using XBAR
- 6.4.5.8 ePWM Synchronization Check
- 6.4.5.9 ePWM Application-Level Safety Mechanism
- 6.4.5.10 Online Monitoring of Interrupts and Events
- 6.4.5.11 Monitoring of ePWM by ADC
- 6.4.5.12 HRPWM Built-In Self-Check and Diagnostic Capabilities
- 6.4.5.13 Information Redundancy Techniques
- 6.4.5.14 ECAP Application-Level Safety Mechanism
- 6.4.5.15 eQEP Quadrature Watchdog
- 6.4.5.16 eQEP Application-Level Safety Mechanisms
- 6.4.5.17 QMA Error Detection Logic
- 6.4.5.18 eQEP Software Test of Quadrature Watchdog Functionality
- 6.4.6
Analog I/O
- 6.4.6.1 Software Test of Function Including Error Tests
- 6.4.6.2 DAC to ADC Loopback Check
- 6.4.6.3 ADC Information Redundancy Techniques
- 6.4.6.4 Open and Short Detection Circuit for ADC
- 6.4.6.5 Software Readback of Written Configuration
- 6.4.6.6 Periodic Software Readback of Static Configuration Registers
- 6.4.6.7 ADC Signal Quality Check by Varying Acquisition Window
- 6.4.6.8 ADC Input Signal Integrity Check
- 6.4.6.9 Monitoring of ePWM by ADC
- 6.4.6.10 Hardware Redundancy
- 6.4.6.11 Lock Mechanism for Control Registers
- 6.4.6.12 DAC to Comparator Loopback Check
- 6.4.6.13 Lock Mechanism for Control Registers
- 6.4.6.14 CMPSS Ramp Generator Functionality Check
- 6.4.6.15 PGA to ADC Loopback Test
- 6.4.7
Data Transmission
- 6.4.7.1 Software Test of Function Using I/O Loopback
- 6.4.7.2 Information Redundancy Techniques Including End-to-End Safing
- 6.4.7.3 Transmission Redundancy
- 6.4.7.4 Periodic Software Readback of Static Configuration Registers
- 6.4.7.5 Software Readback of Written Configuration
- 6.4.7.6 Data Parity Error Detection
- 6.4.7.7 SCI Overrun Error Detection
- 6.4.7.8 SCI Frame Error Detection
- 6.4.7.9 LIN Physical Bus Error Detection
- 6.4.7.10 LIN No-Response Error Detection
- 6.4.7.11 Bit Error Detection
- 6.4.7.12 LIN Checksum Error Detection
- 6.4.7.13 LIN ID Parity Error Detection
- 6.4.7.14 SCI Break Error Detection
- 6.4.7.15 Communication Access Latency Profiling Using On-Chip Timer
- 6.4.7.16 Software Test of Function Including Error Tests Using EPG
- 6.4.7.17 Software Test of Function Using I/O Loopback
- 6.4.7.18 SPI Data Overrun Detection
- 6.4.7.19 Hardware Redundancy
- 6.4.7.20 FSI Data Overrun and Underrun Detection
- 6.4.7.21 FSI Frame Overrun Detection
- 6.4.7.22 FSI CRC Framing Checks
- 6.4.7.23 FSI ECC Framing Checks
- 6.4.7.24 FSI Frame Watchdog
- 6.4.7.25 FSI RX Ping Watchdog
- 6.4.7.26 FSI Tag Monitor
- 6.4.7.27 FSI Frame Type Error Detection
- 6.4.7.28 FSI End-of-Frame Error Detection
- 6.4.7.29 FSI Register Protection Mechanisms
- 6.4.7.30 Hardware Disable of JTAG Port
- 6.4.7.31 Parity in Message
- 6.4.7.32 I2C Data Acknowledge Check
- 6.4.7.33 I2C Access Latency Profiling Using On-Chip Timer
- 6.4.7.34 PMBus Protocol CRC in Message
- 6.4.7.35 PMBus Clock Timeout
- 6.4.7.36 PWM Trip by MCAN
- 6.4.7.37 Software Test of SRAM
- 6.4.7.38 SRAM ECC
- 6.4.7.39 Bit Multiplexing in SRAM Memory Array
- 6.4.7.40 MCAN Stuff Error Detection
- 6.4.7.41 MCAN Form Error Detection
- 6.4.7.42 MCAN Acknowledge Error Detection
- 6.4.7.43 CRC in Message
- 6.4.7.44 Software Test of ECC Logic
- 6.4.7.45 Timeout on FIFO Activity
- 6.4.7.46 Timestamp Consistency Checks
- 6.4.7.47 Tx-Event Checks
- 6.4.7.48 Interrupt on Message RAM Access Failure
- 6.4.7.49 Software Test of Function Including Error Tests Using EPG
- 6.4.1
C2000 MCU Infrastructure Components
- 7References
- 8f28p55x Summary of Safety Features and Diagnostic
- A Distributed Developments
- B Revision History
6.4.6.4 Open and Short Detection Circuit for ADC
The open and short detection circuit allows customers to detect faults in the ADC input channel. This capability is valid only in single-ended mode. For system integrators using differential mode, the ADC must be configured in 12-bit single-ended mode to perform this test. Error response, diagnostic testability, and any necessary software requirements are defined by the software implemented by the system integrator. This capability is deprecated in few part numbers. Confirm the availability of the feature before using this diagnostic.
The following circuit and configuration, selected by programmable register bits to control switches S1, S2, S3, and S4, allows controlling input ADC channel to test for open and short conditions.
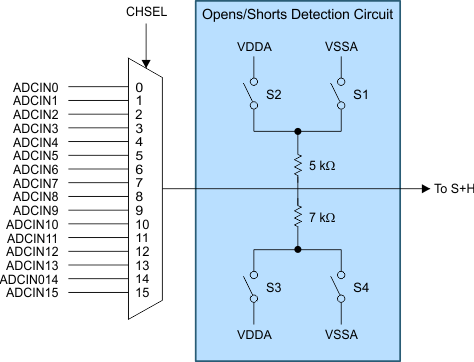 Figure 6-7 Open and Short Detection Circuit
Figure 6-7 Open and Short Detection Circuit| ADCOSDETECT.DETECTCFG | Source Voltage | S4 | S3 | S2 | S1 | Drive Impedance |
|---|---|---|---|---|---|---|
| 0 | Off | Open | Open | Open | Open | Open |
| 1 | Zero Scale | Closed | Open | Open | Closed | 5K || 7K |
| 2 | Full Scale | Open | Closed | Closed | Open | 5K || 7K |
| 3 | 5/12 VDDA | Open | Closed | Open | Closed | 5K || 7K |
| 4 | 7/12 VDDA | Closed | Open | Closed | Open | 5K || 7K |
| 5 | Zero Scale | Open | Open | Open | Closed | 5K |
| 6 | Full Scale | Open | Open | Closed | Open | 5K |
| 7 | Zero Scale | Closed | Open | Open | Open | 7K |