-
Method to Enhance Authentication Security of BQ26100
Method to Enhance Authentication Security of BQ26100
Abstract
In most electronic products, the system vendor needs to ensure some of sub-systems/sub-units (slave) in the system are original and qualified. For example, the smart phone or notebook maker need to ensure the battery pack are original and qualified. This process is to secure their commercial interests, and secure their brand to avoid any artifact issues, because it will hurt their brand greatly once there is any critical safety issue in the field, for example, smart phone is smoking, catching on fire, or even exploded. So, the system vendor needs to authenticate the sub-systems/sub-units. TI BQ26100 is one dedicated authentication IC, with SHA-1 algorithm. This application note introduces a novel method to enhance the authentication security of BQ26100.
Trademarks
All trademarks are the property of their respective owners.
1 Introduction
There are many methods to authenticate the slave. Some methods are listed below.
One simple method is to add one resistor in the slave. The host detects its resistance. And if the resistance is in the expected range, then the host will consider the slave is qualified. This method is simple and low cost, but easy for cheap copy.
Another method is to add one EEPROM device (like TI BQ2022A) in the slave. EEPROM stores some specific data. The host read the data from EEPROM, and compare with the data stored in the host. If they are matched, the host will consider the slave is qualified. But the data is transmitted transparently via communication line. So, it is easy to capture the data, and also easy for cheap copy.
The more complicated method is to add authentication device with SHA-1/SHA-256 algorithm in the slave. The host will generate a serial of random data (challenge), and send to the slave. Both host and slave will use the same challenge, key and function to calculate the result (digest). Then the host will read the digest from the slave, and compare with the digest that host itself calculates. If they are matched, the host will consider the slave is qualified. With this method, it is not easy for cheap copy.
The following section describes the BQ26100 and SHA-1 in detail.
2 BQ26100 and SHA-1 Introduction
Figure 2-1 is the simplified schematic of BQ26100. BQ26100 applies single wire communication SDQ. SDQ pin is a multi-functional pin: communication pin and power supply pin.
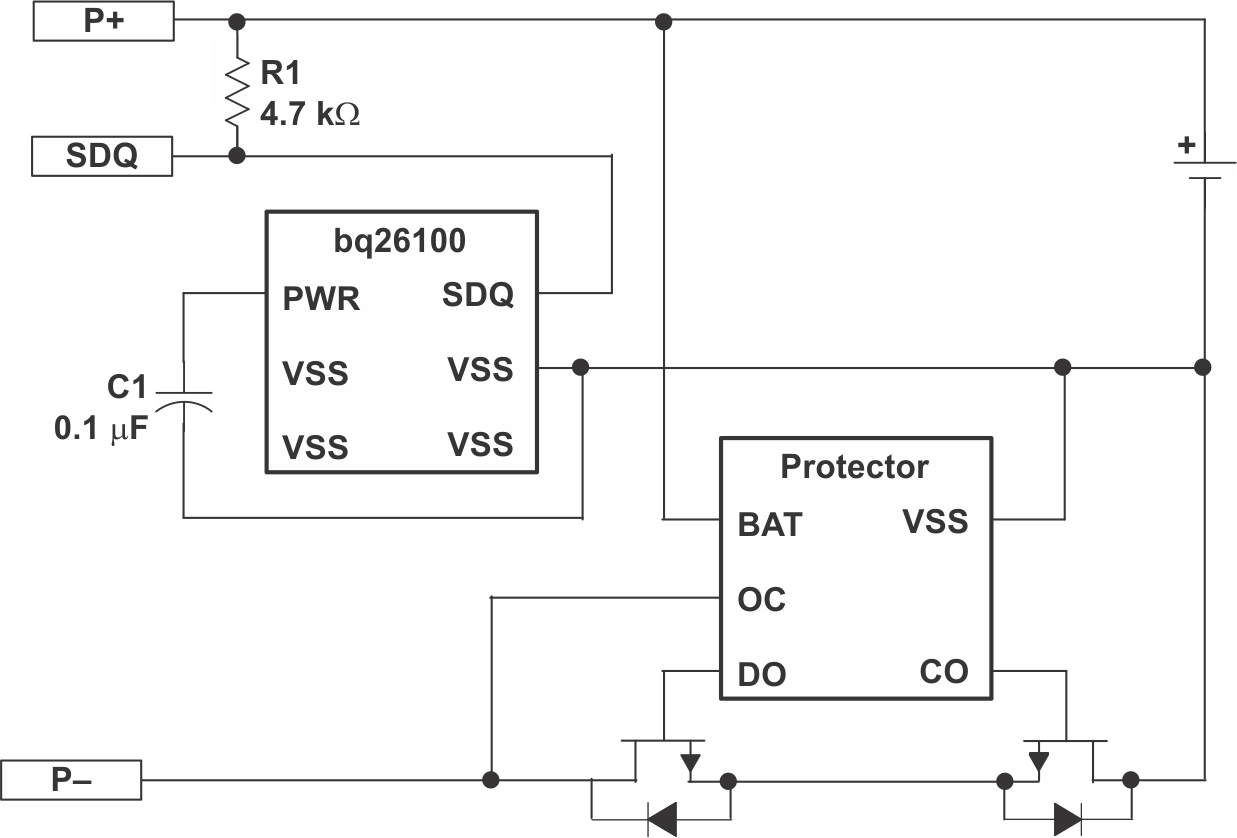 Figure 2-1 Simplified Schematic of
BQ26100
Figure 2-1 Simplified Schematic of
BQ26100BQ26100 embeds SHA-1 authentication algorithm. Figure 2-2 shows the flow of SHA-1 authentication.
- The host and slave store the same 16 bytes key.
- The host generates 20 bytes random number as challenge. And also send to the slave.
- Both the host and slave use the same key, the same challenge, the same function SHA-1 to calculate the results: 20 bytes digest.
- The host read the result from the slave.
- Host compares the two results.
- If the two digests are matched, then consider the slave is qualified.
From the steps above, we can see that the 20 bytes challenge and 20 bytes digest are detectable, and are transmitted transparently through communication line, as shown in Figure 2-2 with green arrows. The third party can easily detect those data with logic analyzer. But theoretically, even they know the challenge and digest, they cannot deduce the SHA-1 key. This is the advantage of SHA-1 authentication.
To enhance the security level of SHA-1 authentication, one simple method is that the host use the first 20 bytes digest as another 20 bytes challenge and run authenticate for the second time.