SWRA780A September 2023 – February 2024 CC3300 , CC3301
3.5 Secured Host Interface
Important: Host interface security is still under design and must
be implemented in next phases. Nevertheless, host interface security is brought here
for reference.
Secured host interface focuses on the traffic that is transferred from the host MCU/MPU subsystem to the CC33xx companion IC. A potential hacker can hijack the interface HW lines and use those lines to read confidential information like encryption keys, payload of data units and more. A hacker can also write to those lines and cause unwanted behavior of the device or give misleading events to the host controller as is illustrated in Figure 3-3.
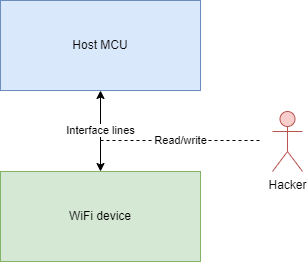 Figure 3-3 Host Interface Threat
Figure 3-3 Host Interface Threat