SWRA780A September 2023 – February 2024 CC3300 , CC3301 , CC3301MOD , CC3351MOD
2 Internet of Things (IoT) Products and Security
An IoT device is by nature a network-connected device, and therefore can serve as a gateway to malicious access to sensitive data, such as surveillance videos, or control over actuators, such as door locks. To achieve good security for an internet-enabled product, a security assessment must be performed on the specific product and the system-level requirements. This assessment identifies the involved assets, analyzes the environment as well as intended and unintended potential usages of the product, and thereby detects potential vulnerabilities of the product.
This assessment helps the developer define the best protection scheme using the available security capabilities.
The environment, the assets, and the processes are different from one product to another, but generally for IoT devices there are some common exposure points:
- Physical access (with or without the ability to manipulate hardware interfaces)
- Local network connectivity
- Internet (or intranet) network connectivity – not covered in this document
Figure 2-1 illustrates the common exposure points of an IoT-connected product.
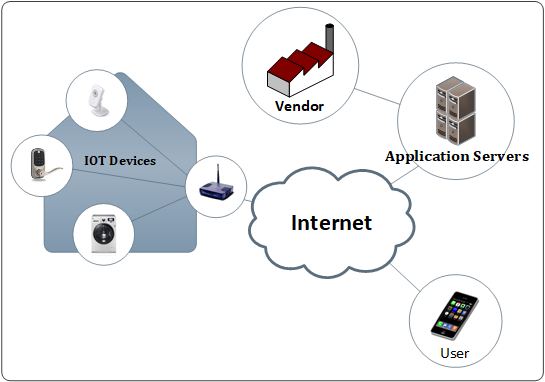 Figure 2-1 IoT Device Exposure
Points
Figure 2-1 IoT Device Exposure
Points