SWRA779 September 2023 CC3300 , CC3301
4.1 Protocol Overview
Regardless of what hardware interface is used, the traffic is carried over a well-defined protocol. Each hardware interface uses a different wrapper that implements the specific hardware protocol but the actual payload is the same. The protocol details are listed in this section for completeness but do not require any porting efforts from the developer/integrator.
The protocol consists of several command options:
- Generic command format. In this
command, no host_rx is involved
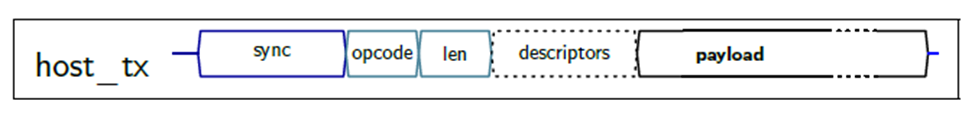 Figure 4-1 Generic
Command
Figure 4-1 Generic
Command - send() or sendto() command format. The device returns a
status response indicating the success of the command
 Figure 4-2 Send or Sendto
Command
Figure 4-2 Send or Sendto
Command - recv() or
recvfrom() command format, in which the response contains data packet
or not
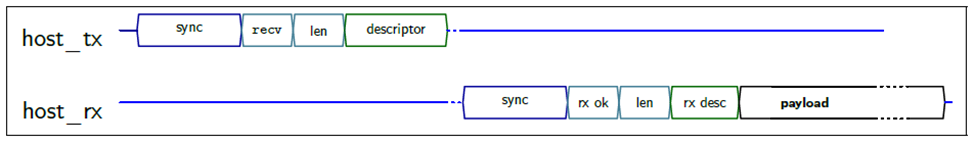 Figure 4-3 Recv or Recvfrom
Command
Figure 4-3 Recv or Recvfrom
Command - read_status sequence
format, where the host requests the device to provide an immediate status
 Figure 4-4 Read_status
Command
Figure 4-4 Read_status
Command - cnys sequence format,
where the host requests the device to provide a single, highest priority,
packet
 Figure 4-5 Cnys Command
Figure 4-5 Cnys Command
Table 4-1 describes the different command fields.
Table 4-1 Protocol Structure
| Field | Description |
|---|---|
| SYNC | Constant pattern which is used to synchronize the boundary of a command or response |
| Opcode | Identifies the command or response (depends on direction of the traffic) |
| Length | Length of everything that follows this field |
| Descriptors | Depending on the opcode/command, descriptors may follow that provide further information. For example, for a send() operation, the descriptor identifies the socket, flags and length of the actual payload. It also requires a Tx status response field |
| Payload | Anything else that the command needs |
| CNYS | Constant pattern which triggers the device to respond with received data or event |